For anyone who understands the value of data privacy, adopting the best practices for cybersecurity can never take the back seat. Think about this; September of 2023 witnessed 71 publicly disclosed security incidents.
This led to the compromise of a staggering 3.8 billion records, bringing the year’s total breaches to an upwards of 4.5 million. These estimates are a stark reminder of the ever-evolving and escalating nature of cyber threats.
To curb these threats, getting an SSL certificate became a necessity. Here’s where technologies like SSL inspection come into play. SSL inspection decrypts data to expose any hidden threats in encrypted traffic and preserve the integrity of information.
In this guide, we will walk you through how it works. We will also touch on the benefits of SSL inspection and most importantly, the best practices.
Table of Contents
What is SSL Inspection?
SSL inspection is also known as HTTPS inspection, TLS inspection or HTTPS interception. It is a critical cybersecurity process that involves the scrutinizing of encrypted traffic to identify any attempts to exfiltrate data, prevent malware attacks and block some websites.
The technique used here is akin to an on-path attack on the network connection, a capability that is embedded in most corporate networking devices, threat management tools and firewalls. Now, SSL inspection works by establishing two separate encrypted connections.
This effectively impersonates not just the client but also the server and allows the inspection process to scan for and neutralize any malicious threats. All this process is done with the client not having any knowledge of the intermediary presence.
So quite simply, during a HTTPS inspection, the inspection tool creates two SSL connections while simulating direct communication between the client and server as the traffic is diverted to the inspection tool. Since the inspection tool impersonates the website in this process, it gets the privilege to not only monitor but also modify and if needed block the content.
What are the Benefits of SSL Inspection?
The proliferation of SSL certificate authorities has not only made it easier for attackers to get valid SSL certificates. It has also made it cost-effective. And with more than 95% of Google traffic now encrypted, the need to inspect SSL traffic has never been great. Here are five benefits you get from SSL inspection;
- Improved Security against Threats in Encrypted Traffic: To appear legitimate, more and more malware authors are using encryption to conceal their exploits. To block attempts to infiltrate your network, HTTPS interception now allows you to decrypt SSL traffic. Also, it allows you to analyze the traffic to identify and neutralize hidden threats in real-time.
- Support for Multi Layered Defense Strategy: For many organizations that have implemented HTTPS inspection, the biggest advantage is the fact that it complements existing security measures. This helps you create a comprehensive multi-tiered defense strategy that significantly improves your company’s overall security posture.
- Preventing Data Breaches and Unauthorized Access: This is self-explanatory but still worth a mention. SSL inspection helps you detect concealed malware and thwart malicious characters trying to bypass your defenses. This way, it helps you ensure that all your sensitive pieces of information remain untampered with.
- Ensuring Regulatory Compliance: Today, many industries are bound by stringent compliance requirements in regard to data protection. HTTPS interception helps you meet these standards. It also guarantees that employees do not leak confidential data unknowingly.
- Visibility into Outbound Communications: With SSL inspection, you do not just enjoy the luxury of being able to monitor outbound traffic. It also allows you to get an understanding of the data transmitted outside your network, a key aspect in being able to identify and address any potential risks, both intentional and accidental.
What is SSL Interception?
Simply put, SSL interception is the practice of intercepting encrypted SSL/TLS traffic. The intercepted traffic may then be altered for various purposes depending on who intercepted the traffic.
Think of it as eavesdropping on encrypted traffic and it can be achieved by putting in place an intercepting party which acts as the middleman between the sender and receiver. In the cybersecurity aspect, this is known as a Man-in-the-Middle or MiTM.
Now, SSL interception can be done by both well-intentioned parties and malicious actors. So, it isn’t always considered a malicious MiTM attack unless the intention for conducting it was deemed malicious. Organizations that seek to safeguard their traffic from unauthorized access and cyber threats use SSL interception to monitor traffic and ensure a smooth flow of data without interference from threat actors.
What is the Need for SSL Inspection?
HTTPS which encrypts the data transmitted between users’ browsers and web servers give users some level of security and increase their trust in brands that implement HTTPS. And thanks to several campaigns by major players like Google for webmasters to switch from HTTP to HTTPS, there has been a wide adoption of HTTPS.
Here’s the twist; cybercriminals can also exploit this encryption to conceal their malicious activities. This means that they may be able to launch attacks unsuspected.
In fact, it is estimated that 85% of internet attacks are encrypted. Here is where SSL inspection comes in handy.
Serving as a safeguard against scammers, hackers and fraudsters who may try to exploit encrypted traffic and launch attacks on servers, SSL inspection helps you decrypt and analyze the content within encrypted traffic. This way, organizations cannot only identify potential threats but also neutralize them before they hit intended targets.
Also as earlier mentioned, SSL inspection enables organizations to comply with regulatory requirements and industry standards. Often mandating the monitoring and inspection of network traffic especially for sectors that handle sensitive information like finance and healthcare, these industry standards and regulatory requirements are now easier to comply with, thanks to technologies like SSL inspection.
How Does SSL Inspection Work?
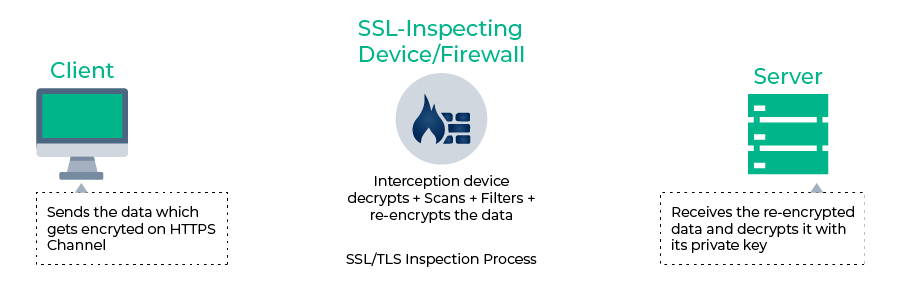
If you’re ready to implement SSL inspection you may wonder, how does SSL inspection work? And, what are the methods of SSL inspection? Here’s a simplified answer;
As earlier explained, SSL inspection makes use of an interception proxy that is positioned between client and server endpoints to decrypt and analyze the traffic. However, decrypting and inspecting all internet traffic is very resource-intensive.
Due to this, many organizations mostly focus on inspecting specific traffic from sources suspected to be malicious. The only problem with this approach is that it isn’t as easy as it sounds to determine the destinations that merit trust and assess their vulnerability to attacks.
To facilitate SSL inspection, there are three methods that are mostly favored; next-gen firewalls, proxies and the TAP method. Each method comes with its advantages and limitations.
This means that in the end, your chosen method for SSL inspection will be influenced by factors like your organization’s needs including the volume and sensitivity of your traffic as well as your capacity for processing power and bandwidth. The most important thing is to strike the right balance between security and operational efficiency. Here’s what you need to know about the methods of SSL inspection;
- Next-Gen Firewalls (NGFW): These methods allow for the streaming of traffic for inspection. They’re quite efficient on this. However, they may struggle to handle high volumes of traffic.
- Proxies: Proxies establish separate connections between the client and server. This enables thorough inspection but this approach may introduce slight delays due to the additional step.
- TAP Mode: This method copies traffic as it flows. It allows for offline analysis but requires additional resources for the analysis phase even though it doesn’t interfere with live traffic.
What are the SSL Inspection Best Practices?
Quite literally, HTTPS inspection has been a game changer for those concerned about their sensitive data potentially being stolen by programs that mimic legitimate traffic. But, to get the most out of this process, there is no better way than following SSL inspection best practices.
Adhering to these best practices ensures that you can enhance your web security infrastructure without any infringement. Here are four HTTPS inspection best practices to know about before implementing the technology;
- Inbound vs. Outbound Inspection: Inbound inspection is focused on the traffic that is going towards the client. It safeguards internal servers through Intrusion Prevention System (IPS) protections. On the contrary, outbound inspection inspects the traffic that is directed to the server. It is best to create a clear distinction between the two to ensure comprehensive protection against potential threats from both directions.
- Respect for Legitimate Privacy Concerns: There are some pieces of information that are protected by regulations like GDPR, PCI DSS, and HIPAA. To best use HTTPS interception, recognize and respect the privacy concerns that pertain to such data. To achieve this, you will want to configure your HTTPS inspection rules in a way that allows you to exclude traffic that is likely to contain sensitive data. This is especially crucial for industries like finance, and healthcare which are bound by data protection regulations.
- Implement Recommended Bypass List: You can reduce unnecessary network latency by implementing a recommended bypass list. This can be helpful as not all traffic requires SSL inspection.
- Gateway Certificate Implementation: To build trust between endpoint browsers and security gateway certificates, import gateway certificates. This will help you eliminate browser warnings that may otherwise erode user confidence.
Apart from the cybersecurity advantages that SSL inspection provides, it is imperative that enterprises take into account pragmatic factors like SSL Certificate Price. This guarantees a thorough approach to protecting your digital assets while striking a balance between security efficacy and financial concerns.
It’s a Wrap!
We get it; it may not seem easy to implement SSL inspection. Nonetheless, it remains a key part of not only ensuring that you comply with regulations but also safeguarding your confidential data. For the best experience, don’t just implement HTTPS inspection. See to it that you follow the best practices for SSL inspection.


