Everything You Need to Know About SSL Certificates in One Place
Did you know 95% of Google’s traffic is encrypted? Hence, the importance of SSL certificates today cannot be overstated.
With consumers’ ever-growing reliance on e-commerce, data sharing, and online transactions, SSL certificates, including cheap SSL options, have become crucial in authenticating website identities and establishing encrypted connections.
Website owners demonstrate commitment to data protection with a valid SSL certificate. It fosters an environment where customers can confidently engage in online business interactions.
If you’re in business, the security and integrity of online communications are paramount if you want to stay a step ahead of competitors. That’s where SSL, the acronym for Secure Sockets Layer, fits in perfectly. It has become an indispensable technology that forms the bedrock of trust and protection on the web.
What is an SSL Certificate?
Secure Sockets Layer, SSL certificate is a digital certificate that secures encrypted connections between web servers and browsers, enhancing HTTPS security. It protects confidential data, guaranteeing a safe online environment for transactions and interactions.
Encryption technology ensures sensitive data exchanged cannot be intercepted or manipulated by malicious individuals. That’s not all; SSL Certificates benefit businesses in more than one way.
The most obvious benefit is authentication and verification of website identities. This ensures users communicate only with intended servers, not imposters, empowering businesses to cultivate customer trust and loyalty.
Another benefit is scrambling of data before transmission. This ensures that even if hackers intercept data, they receive it in an unreadable format, rendering it useless.
A further benefit is improved online visibility. Search engines prioritize secure websites, including those with valid SSL certificates, in search algorithms and rankings. As a result, websites are more likely to move up on Search Engine Results Pages (SERPs), enhancing visibility and potentially attracting more organic traffic.
And, though helpful, SSL is an older technology that comes with few security flaws. So, TLS was introduced to fix existing SSL vulnerabilities. It offers enhanced encryption protocols and key exchange methods, making it a preferred choice for secure internet communication.
Types of SSL/TLS Certificate and Validation Levels
SSL certificates come in different types to meet various website needs. Three common SSL certificate types are Single Domain, Wildcard, and Multi-Domain certificates.
-
Single Domain Certificates
Single Domain Certificates secure one domain or subdomain, providing secure connections for a specific domain without variations.
-
Wildcard Certificates
Wildcard Certificates secure a domain and its subdomains with a single certificate, eliminating the need to manage several certificates for each subdomain. Many web owners opt for cheap wildcard SSL certificates for their cost-effectiveness and ease of administration.
-
Multi-Domain Certificates
Multi-Domain Certificates can secure multiple domains or subdomains with one certificate, simplifying management and reducing costs. A cheap multi-domain SSL certificate may be preferred for operating multiple websites or services across various domains.
SSL certificates also have different validation levels, determining the verification extent the Certificate Authority (CA) performs.
-
Domain Validation (DV)
Domain Validation (DV) SSL certificates, the simplest and quickest to obtain, involve the CA verifying only domain ownership to ensure the applicant controls the website’s domain. The applicant receives an email with a unique verification link or a code for the website.
-
Organization Validation (OV)
Organization Validation (OV) SSL certificates offer higher trust, with the CA conducting a more rigorous validation process. It includes verifying domain ownership and authenticating the organization’s information through public databases, government records, or other trusted sources. Contacting the applicant via phone or requesting specific documentation is also a part of this process.
-
Extended Validation (EV)
Extended Validation (EV) SSL certificates provide the highest trust level and visual security indicators. The CA performs a stringent verification process, including domain ownership, organization details, legal existence, and physical location. This may involve legal opinion letters, bank references, and additional checks to establish authenticity and trustworthiness of organization.
How Does an SSL/TLS Certificate Work?
SSL certificates use encryption technology to ensure privacy and security of confidential data shared online. Encryption’s fundamental function is encoding information, ensuring only intended and authorized individuals access shared information.
SSL certificates work with symmetric and asymmetric encryption. It’s vital to comprehend the variations between symmetric and asymmetric encryption techniques. Here’s the difference explained in simple terms:
-
Symmetric Encryption
Symmetric Encryption requires a single key for encrypting and decrypting data. This approach’s challenge is securely exchanging the key beforehand. SSL Certificate uses symmetric encryption in the session key after the initial handshake. Symmetric algorithms include RC4, IDEA, Twofish, Serpent, CAST5, TDES, and Blowfish.
-
Asymmetric Encryption
Asymmetric Encryption solves the key exchange problem by using a pair of keys: a public key and a private key. In asymmetric encryption, an SSL certificate initiates communication, known as an SSL handshake, with algorithms like RSA, DSA, ECC, and PKCS.
The public key is freely distributed, while the private key is securely held by the intended recipient, ensuring confidentiality without a shared secret key exchange.
When browsers establish secure connections with a website, they request the server’s SSL certificate, storing the website’s public key. The public key encrypts data sent, decryptable only by the corresponding private key, which the website holds.
SSL Handshake Process
On secure websites, browsers and servers engage in handshake processes. The handshake processes help establish secure connections and ensure that data remains confidential. Here are the steps showing how an SSL handshake works to establish a typical secure connection:
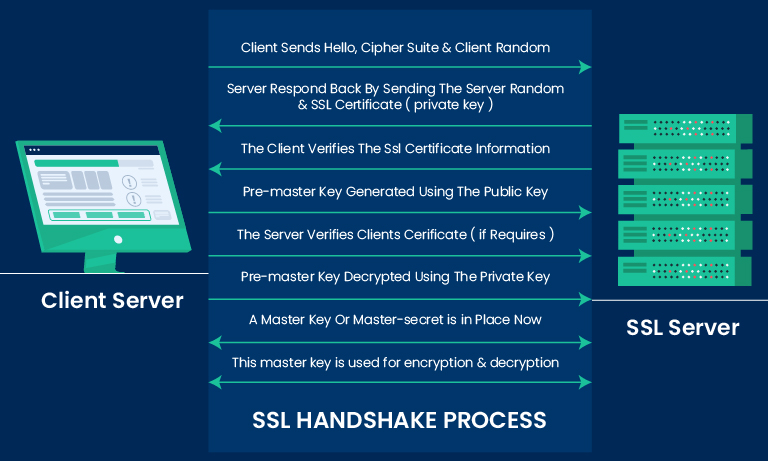
- Client Hello: The handshake process begins with browser sending a “Hello” message to the server. It also states its preferred SSL/TLS version and encryption algorithms.
- Server Hello: The server responds with its chosen SSL/TLS version and cipher suite. This specifies the encryption algorithm and other parameters for the secure connection.
- Certificate Exchange: Server sends its SSL certificate to verify authenticity.
- Client Authentication (Optional): Server may request client authentication using a client certificate for extra security. Though optional, this step helps add an extra layer of security.
- Pre-master Secret Exchange: The client generates a pre-master secret, encrypts it with the server’s public key from the SSL certificate, and sends it back to the server.
- Session Key Generation: Both the client and server independently derive the session key from the pre-master secret and other random values exchanged during the handshake.
- Encryption: With the session key in hand, both client and server can now encrypt and decrypt the data exchanged during the secure session, ensuring confidentiality.
- Finished Messages: Both parties exchange “Finished” messages containing a hash of all previous handshake messages to confirm a secure and tamper-free connection.
The handshake process involves multiple steps but typically concludes within a few seconds, establishing a secure connection.
Certificate Authorities and Certificate Chains
When issuing SSL certificates, Certificate Authorities (CAs) play a vital role. They issue these digital certificates to safeguard trust and integrity of online communication. CAs are trusted third-party entities that validate authenticity and identity of websites or organizations requesting SSL certificates.
This trust hierarchy ensures SSL certificates, validating authenticity of websites, are issued by trusted entities. The trust hierarchy starts with the root certificate, the highest authority level in the chain. Think of the root certificate as the foundational pillar on which the entire web of trust is built.
Root certificates are issued and signed by root CAs, trusted entities built into web browsers and operating systems. These root CAs verify the identity of other CAs, with their certificates pre-installed in browsers, creating a foundation of trust for all SSL certificates issued by intermediate CAs.
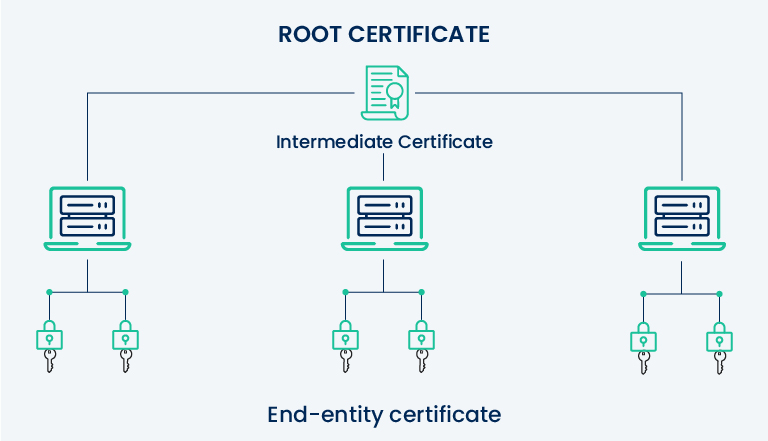
Intermediate CAs bridge the gap between root CAs and end-entity certificates. They have the authority to issue SSL certificates to website owners. While web browsers do not directly trust intermediate CAs, their certificates are validated through the chain of trust inherited from root CAs.
Certificate chains, also known as certificate hierarchies, link SSL certificates in a series of trust relationships. When a website’s SSL certificate is presented to a browser during the secure connection process, the browser checks the entire chain of trust to verify the certificate’s authenticity.
The browser examines the website’s SSL certificate, signed by an intermediate CA, then verifies the intermediate CA’s certificate, signed by a trusted root CA. This process continues until the browser reaches a root CA certificate in its trust store.
The SSL certificate is trustworthy if the entire chain is valid and traces back to a trusted root CA. To maintain trust and integrity, CAs undergo rigorous auditing and compliance processes. Independent auditors assess CAs’ adherence to industry standards and best practices, ensuring strict protocols are followed when issuing SSL certificates.
SSL Certificate: Renewal and Revocation
SSL certificates, like all security measures, have an expiration date. Just as we renew our passports to continue enjoying the benefits of international travel, SSL certificates must be renewed to maintain a website’s secure status. Here’s a breakdown of the typical process of how to renew SSL certificates.
- Identifying expiration date: The SSL certificate expiration date information is usually provided by the certificate authority (CA) that issued the certificate. You may also identify your certificate’s expiration date by checking the certificate details present in the padlock or tune icon. You will find the date under the “Validity period” section on the micro pop-up window.
- Contacting certificate authority: Depending on server settings or CA, one may be able to set automated renewal processes. If that isn’t the case, keep a keen eye on the expiration date. Contact the CA as this date approaches so they can guide you through the renewal process. This may involve submitting updated information or undergoing a validation process to ensure the website’s authenticity.
- Installing renewed certificate: A new SSL certificate is issued once the authority approves the renewal request. Installing this renewed certificate promptly is essential to maintain uninterrupted, secure connections with website visitors.
- Compromised private key: The private key associated with SSL certificate is very important for secure website communications. If it is compromised, CA may decide to revoke it. This is done to prevent impersonation and unauthorized access to sensitive information.
- Incorrect or outdated information: SSL certificates contain information about website owners. Typical information includes domain name and organization details. SSL certificates may be revoked if there are notable changes to this information or if it becomes outdated. You’ll need a new one to ensure accurate and up-to-date identification.
Owing to the losses that come with a bad or revoked SSL certificate, you will want to know how to avoid the consequences. Here are a few helpful recommendations to check if certificate was revoked:
- Check Certificate Revocation Lists (CRLs): Certificate authorities maintain a list of revoked certificates. These are known as the CRLs. Access these CRLs via CA’s website. Alternatively, download the CRL and compare it with the certificate in question. Note that CRLs require regular updates, and relying solely on them may result in outdated information.
- Online Certificate Status Protocol (OCSP): OCSP is an online protocol providing real-time certificate revocation status. On enquiring about SSL certificate validity, an OCSP query is sent to OCSP responder to check the particular certificate with reputable CA. An OCSP response is then sent back with either ‘revoked’, ‘good’, or ‘unknown’ certificate status. This method ensures more up-to-date information than CRLs.
- Certificate Transparency Logs: Certificate Transparency (CT) logs are publicly accessible records providing information about SSL certificates issued by trusted authorities. These logs can be searched to verify a certificate’s existence and status. While CT logs don’t explicitly indicate revocation status, they contribute to transparency and allow monitoring of certificate issuance.
Implementing SSL Certificates
If you’re a new web owner, installing SSL certificate correctly may seem frustrating. Good news, it’s not too complicated. Here’s how to implement SSL on web servers:
- Choose a Trusted Certificate Authority (CA): You do not want to run into issues after investing in an SSL certificate, so this is an important step you should not skip. Trusted CAs have a reliable vetting process and are recognized by major web browsers. Check reviews and track records to compare CAs.
- Generate a Certificate Signing Request (CSR): Generate a Certificate Signing Request (CSR) on web server to get SSL certificate. The CA will need the CSR to create a unique SSL certificate for your website.
- Submit the CSR to the CA: After generating CSR, submit it to selected CA. Be sure to follow their specific instructions for submitting the CSR. The CA will validate the information provided and issue the SSL certificate.
- Install the SSL Certificate on your Web Server: The installation process for SSL certificate varies depending on web server software (e.g., Apache, Nginx, Microsoft IIS, etc.).
Here are some tips for configuring SSL the right way;
- Choose the Right SSL Certificate Type: SSL certificates come in various types. Consider level of trust and validation the website requires. Also, consider budget when selecting appropriate SSL certificate type.
- Enable HTTPS for All Website Pages: To maximize security benefits of SSL, enable HTTPS (Hypertext Transfer Protocol Secure) for all pages on website.
- Redirect HTTP Traffic to HTTPS: To enforce SSL usage, configure web server to redirect all HTTP traffic to secure HTTPS version of website. Do this via server configurations. Alternatively, employ redirect rules in .htaccess file (for Apache) or server block configuration (for Nginx).
- Keep SSL Certificates Updated: All SSL certificates come with validity period, which can be as low as 3 months to about 13 months. Actively monitor expiration date or use automated SSL certificate renewal to avoid disruptions in SSL functionality.
You can test the configuration to ensure SSL certificate is working as intended. Here are some tips on how to troubleshoot common issues;
- Test SSL Installation: After installing SSL certificate, perform thorough test to ensure its proper functioning. Use online SSL checker tools to verify the certificate’s validity, check for correct installation, and confirm no errors or warnings are present.
- Mixed Content Warnings: When migrating from HTTP to HTTPS, ensure all elements on website (images, scripts, CSS files) are loaded securely. Mixed content warnings occur when insecure elements are loaded on secure pages, potentially compromising security. Use browser developer or online tools to identify and fix mixed content issues.
- Intermediate Certificate Chain: Sometimes, SSL installation issues arise due to missing intermediate certificates. Intermediate certificates establish a chain of trust between your SSL certificate and CA’s root certificate. Make sure to install the intermediate certificates along with SSL certificate to ensure proper validation.
- SSL Certificate Compatibility: Ensure certificate is compatible with major web browsers and operating systems by testing it on multiple browsers and different devices. If compatibility problems occur, contact CA for assistance in resolving the issue.
Best Practices for SSL Certificates
SSL certificates establish encrypted connections between web browsers and servers, ensuring data transmitted remains confidential and integral. They provide users with visual cues, such as padlock/tune icon or “https” in the URL, instilling trust and confidence in online interactions.
SSL certificates protect against eavesdropping, data tampering, and impersonation attacks by encrypting sensitive information. They are particularly vital when handling financial transactions, personal data, login credentials, or any confidential information.
But implementing SSL isn’t enough. It is essential to stick to the best practices for SSL certificates which include;
-
Staying Updated with Security Standards:
To maintain a robust security posture, staying updated with the latest security standards and best practices for SSL certificate management is imperative. Cybercriminals continually devise new methods to exploit vulnerabilities, making regular updates crucial to mitigating risks. Monitor industry trends, security advisories, and guidelines from reputable sources, like the Certificate Authorities/Browser Forum (CA/Browser Forum) or the Internet Engineering Task Force (IETF). Implementing these updates can help prevent potential security breaches.
-
Choosing Trusted Certificate Authorities:
Ensure SSL certificates are obtained from trustworthy Certificate Authorities (CAs) who follow stringent validation procedures. Proper validation confirms the authenticity and legitimacy of the certificate issuer, reducing the risk of falling victim to phishing or fraudulent websites. It’s also crucial to periodically verify certificates’ expiration dates and validity to prevent unintended security lapses.
-
Implementing Strong Encryption Protocols:
SSL certificates rely on encryption protocols to establish secure connections. Ensure certificates utilize robust encryption algorithms, such as Advanced Encryption Standard (AES), with a minimum key length of 128 bits or higher. Stay informed about any vulnerabilities or weaknesses discovered in encryption protocols and promptly switch to more secure alternatives when necessary.
-
Regularly Monitoring SSL Certificate Expiration:
SSL certificates have finite life spans and require regular monitoring to prevent unintended expiration. Expired certificates can disrupt online services, lead to warning messages for users, and expose websites to potential attacks. Establish a system that proactively tracks certificate expiration dates and sends notifications well in advance, allowing ample time for renewal and seamless continuity.
Conclusion
SSL certificates secure online communication and protect sensitive data. They’re widely used to establish encrypted connections to safeguard information from unauthorized access and interception. This functionality is especially important for websites that handle sensitive information like personal details and financial transactions. Implementing SSL certificates enhances data privacy and builds trust among users, ensuring their information is handled with the utmost security. So, switch from unsafe HTTP to secure HTTPS if you’re serious about building trust among your audience. Buy SSL certificates from globally trusted Certificate Authorities at CheapSSLShop.
Related Post:


